
Truth be told, I find it difficult to talk about YubiKeys. It’s a hardware authentication device that supports multiple security protocols to protect access to digital resources. I mind security a lot. I should care about using YubiKeys. Yet, I struggle to find a preference to use them.
That’s not to say YubiKeys aren’t useful. Yubico, the company that makes these YubiKey devices, has been in business for 14 years and currently sells about 12 variants of these hardware. Their devices are still relatively niche, though the company has sold over 28M of them according to their 2023 Annual Report.
The challenge with the YubiKey is explaining how it works, why one would need it, and how it would benefit them. It is already hard to sell this to tech-savvy users, let alone those who are less tech-savvy. I think the latter group probably will be worse off trying to grapple with something they don’t quite understand how to use. This is a product for tech-savvy users.
My focus in this blog post is not so much a product review as it is an education in YubiKey technology and how one might use YubiKey devices. I assume you understand about password security and OTPs, as well as an appreciation of the need for security in our digital lives.
First, YubiKeys does a number of different security things. That’s the part about it supporting multiple security protocols. That’s also why those unfamiliar with YubiKeys may be unclear about what exactly it does. YubiKeys does a few more things than those I’m going to dive into here.
One of the common uses of YubiKeys is as a hardware OTP authenticator. Instead of retrieving OTPs via SMS or emails, YubiKeys can be used to generate TOTP-based one-time codes which are supported by many online services, including Google, Microsoft, and Facebook.
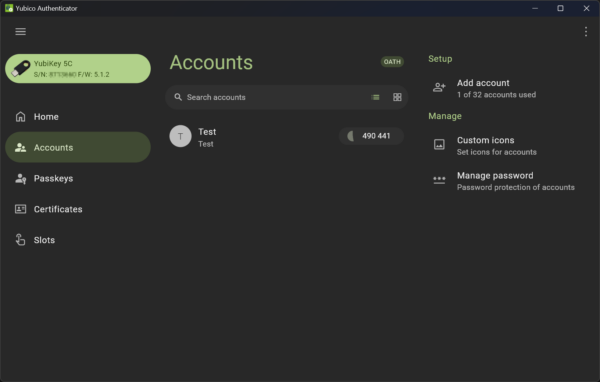
TOTP-based one-time codes are far more secure than getting codes via SMS or email. Both SMS and email messages are easily intercepted. They aren’t secure at all. Yes, including SMS, which many people assume is safe since banks are using them. (Banks are, in fact, trying to move away from using SMS for sending OTP.)
There are several kinds of OTPs. The above mentioned TOTP stands for Time-based One-Time Password. It is only valid for a specific time period. Another popular OTP scheme is HOTP, which stands for HMAC-based One-Time Password, and is valid until the code is used (or a newer one has been used). Both TOTP and HOTP are IETF RFC standards.
YubiKeys also support Yubico’s own OTP scheme. It’s called Yubico OTP. Apart from using it as a OTP in a typical 2FA configuration, Yubico OTP can also used standalone, i.e. as a replacement for usernames and passwords. Yubico OTP is proprietary and support is not anywhere as common as standard TOTP or HOTP.
You may be aware that there are many authenticator apps that can generate OTPs. My favourite password manager supports OTP. There are other popular options, including both Google Authenticator and Microsoft Authenticator. Why would one need a YubiKey? I’ll come back to this question later.
Another authentication method that has gained traction in recent years is Passkeys. The idea is that Passkeys replaces passwords, allowing you to login to online services without needing a password. Passkeys sell the idea of a password-less future. At its heart, Passkeys uses public key cryptography. There is still some “secret material” (i.e. secret key) that is kept with you in the devices you own, and typically protected by a PIN or biometric. Public key cryptography is used to authenticate you with an online service.
Passkeys are great. I’ll skip over related-topics like FIDO2 and WebAuthn and instead just jump to its benefits. Passkeys enable you to login to your favourite websites without passwords. You will need your device, which stores or has access to the secret keys required to perform public key cryptography, and a PIN or biometric to unlock the secret keys. That’s great. You get 2FA, something you have (secret key), and something you know (PIN) or are (biometric).
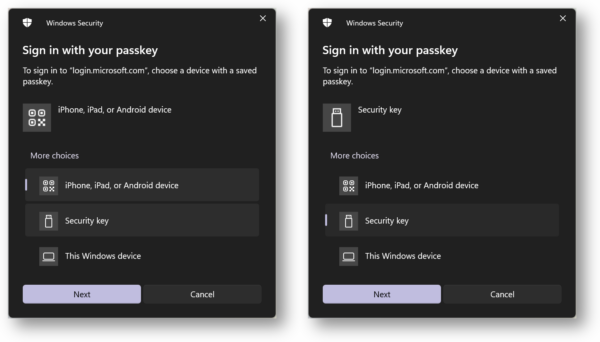
Using Passkeys, logins to supported online services such as microsoft.com will require the YubiKey to be present. Passkeys can be used as a replacement for entering passwords. You can even skip having to enter your username.
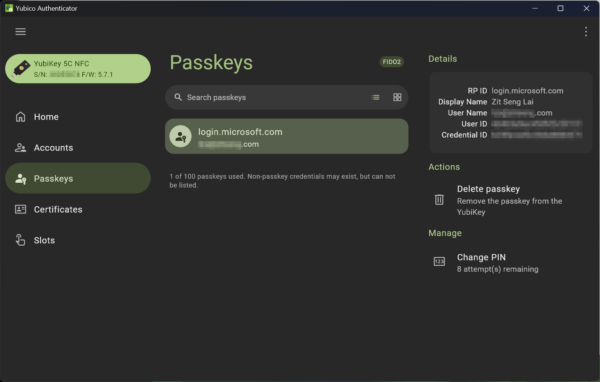
More importantly, Passkeys are immune to phishing attacks. Passkeys can’t be used on a wrong website. You could be fooled to enter your username in a fake website, but the Passkey would not work. You can’t create a bad password with Passkeys because Passkeys don’t use passwords. Websites like microsoft.com will even allow you to remove passwords from your account, so there is no way for anyone to hack your account via a conventional password login.
However, like OTPs, there are other apps that can handle Passkeys. My favourite password manager supports Passkeys. In fact, Windows 10 and 11 also support Passkeys. Why would you need YubiKeys?
That is the question that has had me puzzled. It seems the issue comes down to where these secrets are stored, and how they are protected. (Let me just refer to these various types of secrets, or their data contents, as security tokens.)
I don’t know if this is a great reason, but one was offered to me about the benefit of using YubiKeys to store security tokens instead of using an app in your computer. The YubiKey, in most variants of the hardware that Yubico sells, are designed to be attached to your key ring. I am referring to your physical keys, the ones that you use to lock and unlock your doors. With a YubiKey attached with your keys, you will always have the secrets carried with you. It’s not only about them always available with you, but more importantly, they are not (usually) separated from you.
The important benefit of that physical proximity to you is that you are likely to notice if your YubiKey has gone missing or got stolen. There is no way to steal security tokens from your YubiKey without the physically acquiring the device.
On the other hand, security tokens stored in your computer may be stolen through various methods such as with malware. You wouldn’t even know if those security tokens are stolen since your computer itself is still around. Stolen, in this case, doesn’t mean it has been removed; it can simply be copied. This is a high risk. Even for people who are able to take sensible steps to ensure their computers are safe and secure, it is still easy to make mistakes and fall prey to some types of attacks to steal security tokens that could have been better protected by YubiKeys.

In the general case, YubiKey can offer improved security for most users. The main security mechanisms you need are OTPs and Passkeys. The device is small and easy to carry around. It is meant to be attached to your keys in most cases. I don’t recommend those variants that are meant to be permanently attached to your computer, because then there is little difference from storing your security tokens in the computer itself.
YubiKeys have a couple more features that the more advanced security-savvy users may be interested in. This includes support for OpenPGP keys. If this sounds intriguing, I encourage you to check out Yubico’s website.
Regardless of whether you think a hardware security keys like YubiKeys are useful to you, it is prudent that you evaluate how you store your security tokens. There is so much at stake in our digital lives; you need to be careful about protecting yours.
View Comment Policy