
Every new day, there’ll be a new security vulnerability. Often enough, it will be something important that even casual computer users ought to know about. This is one of them. If you’ve been taught to check your browser URL bar to ensure that you’re at the correct site, and where applicable there’s a valid SSL certificate, it seems that might not be enough.
Mark Maunder revealed on the Wordfence blog about a phishing attack that’s recently receiving much attention. This vulnerability basically puts a legitimate looking URL in the browser URL bar, so that you think you’re visiting the correct website the URL purports to be. However, the URL is in reality a unicode-encoded string that uses the same characters as that other website.
Even if you’ve been trained to check the browser URL bar to ensure you’re at the correct website, this vulnerability will still fool you, because as far as your eyes can tell you, you see the same characters. See the screenshot below. The legitimate website for www.epic.com is in the back, while the fake website is in front.
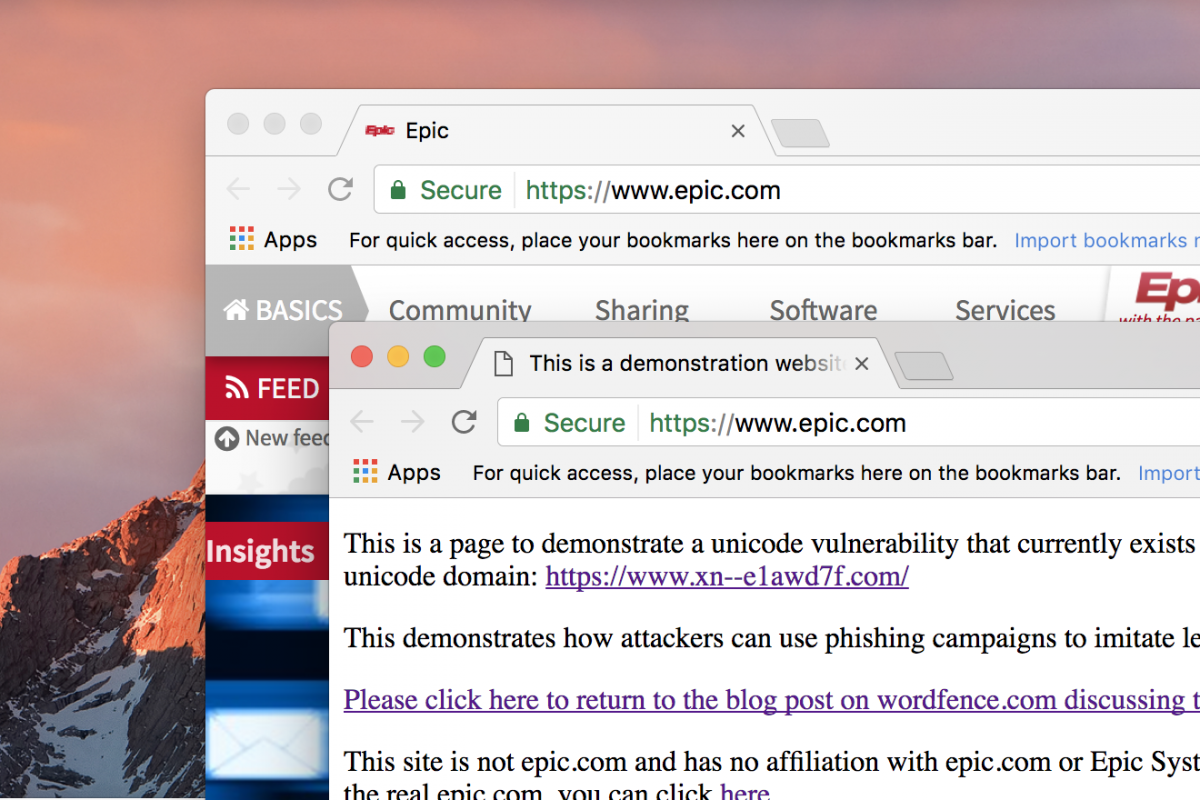
Notice that the fake site even has a good SSL certificate. That’s because its unicode-encoded domain name has been issued with a certificate from Let’s Encrypt. The real domain name of this fake website is actually: www.xn--e1awd7f.com.
But as you can see, Chrome has rendered the unicode-encoded string as something indistinguishable from the real www.epic.com.
What’s the lesson here? Not something terribly new actually. You might have heard, you should just type the full URL into the browser yourself every time to be sure you’re visiting the website you want to go to. Don’t click on email URL links. In this case, the unicode-encoded domain name might appear as a suspicious looking URL in a phishing email, but don’t depend on that, because it’s just all too easy to miss it.
This bug affects Chrome and Firefox. As you’ll read in the Wordfence blog, there is a workaround for Firefox. Unfortunately no fix for Chrome at this time, but it’s certainly coming because a fix has surfaced in the Chrome Canary channel, which is a sort of test release. I expect that a fix will be officially be released in the regular Chrome update channel soon.
A few days ago I wrote a post about how hackers need clueless victims.
Well, the flip-side of it is that sometimes it’s not that easy to stay abreast of all the developments so that you don’t yourself become a clueless victim. There is always something happening. You always have new things to learn.
Sometimes I wonder if I should start a channel, thread, or something that will share particularly relevant bits of cybersecurity developments to help people stay informed?
View Comment Policy