 I’ve been sitting on this information for some time, waiting to get more research done before I publish a post. But since word has come out about how Lenovo preloads what amounts to very bad spyware on their PCs, I thought I should also just go right ahead to spill the beans on the Mac.
I’ve been sitting on this information for some time, waiting to get more research done before I publish a post. But since word has come out about how Lenovo preloads what amounts to very bad spyware on their PCs, I thought I should also just go right ahead to spill the beans on the Mac.
Yes, that’s right. Superfish is bad. The problem with the Mac is only slightly related in that it also involves SSL certificates. It’s also bad, in a different way. I haven’t found out how the situation got to be like this, but I’ll just tell you what is happening.
By now, you should know what SSL is all about. HTTPS, which uses SSL, encrypts your network communication to a server somewhere else on the Internet so that no one can eavesdrop and discover the contents of your communication. You trust that your communication is private, the contents of which is unknown to anyone except yourself and the server you’r communicating with. SSL encrypts the communication and “authenticates” the server.
There is, of course, one more bit to that story. It’s about the Certificate Authority, which certifies the SSL certificates presented by the websites as truly belonging to them. How do you know that the certificate that https://google.com/ presents to you really belongs to Google, and not a fake certificate presented by a random attacker who has managed to intercept your Internet communication? Well, it’s signed by a Certificate Authority, GeoTrust Global CA, in the case of Google. Only the real Google would have such a certificate, because the Certificate Authority will not issue random SSL certificates to anyone else.
Do you see a small problem here? You’ve got to trust the Certificate Authority. The problem with Lenovo’s Superfish is that it installed its own Certificate Authority certificate so that you computer will trust it. (Subsequently, their certificate was also hacked, but that’s another matter altogether.)
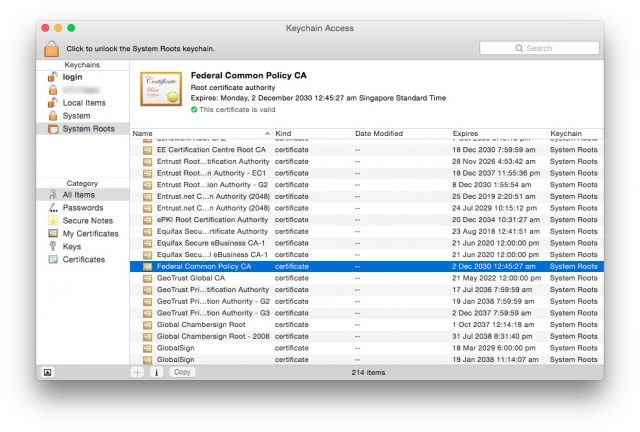
Normally, this is all fine, Superfish’s certificate aside. The Certificate Authorities are usually trustworthy. Usually. Except, when you look into the list Certificate Authorities trusted by the Mac. There are the usual big name Certificate Authorities like Verisign, GeoTrust, Symantec and Thawte. But how about these ones:
- Subject: C=US, O=U.S. Government, OU=FPKI, CN=Federal Common Policy CA
- Subject: C=US, O=U.S. Government, OU=DoD, OU=PKI, CN=DoD Root CA 2
- Subject: C=JP, O=Japanese Government, OU=ApplicationCA
- Subject: C=CN, O=China Internet Network Information Center, CN=China Internet Network Information Center EV Certificates Root
To be clear, the U.S. government has several more Certification Authority certificates installed in the Mac. The Japanese government has at least one more. China Internet Network Information Center doesn’t sound like the Chinese government themselves, but if you check, they are responsible for Internet affairs under the Ministry of Information Industry of the People’s Republic of China. That sounds like an extension of the Chinese government to me.
But governments are the good people right? Erm, I don’t know. There are people who don’t trust their own government. For example, U.S. citizens may be concerned about their NSA (or FBI) spying activities. They are afraid about the NSA being able to break encryption codes.
Well, it turns out that NSA’s job is a lot easier. There are no codes to break. They just intercept your communication, carry out a man-in-the-middle attack, and what else do they need? You think your HTTPS connection is securely encrypted, but wait, couldn’t the U.S. government generate a brand new fake certificate, give it to the NSA, and then serve that to you? Your web browser won’t raise any alarm bells. The SSL certificate is valid, and it is signed by a Certificate Authority that is trusted by your computer.
So, just to get this straight. Not only does the U.S. government have the privilege of intercepting any of your HTTPS connections and present valid, trusted, SSL certificates to you, the Japanese government and the Chinese government have the same privileges.
Let me make this clearer. Any Certificate Authority can generate fake SSL certificates for any website. It’s not very useful unless they are working together with a network operator to get into a position to easily intercept your communication. Or, if they themselves are also a network operator. Are there Certificate Authorities who are also in the network operator business? Yes, yes, just from a cursory glance at the company names, I can see:
- Subject: C=TW, O=Chunghwa Telecom Co., Ltd., OU=ePKI Root Certification Authority
I’ve listed 5 different Certificate Authorities as examples. None of them appear in my Windows PC (Windows 7).
Are these Certificate Authorities, which are found in the Mac, necessary? I highly doubt so. One thing for sure is that it won’t disrupt your web browsing activities, seeing that Windows PCs, without these Certificate Authorities, work just fine. I can appreciate Apple wanting to embed a bunch of their own Certificate Authority certificates (five of them, to be exact), not dissimilar from how Microsoft also embeds their own in Windows PCs.
Sidenote: A Windows 7 PC has 38 Certificate Authority certificates installed. My Mac OS X Yosemite has 217 Certificate Authority certificates installed. (Update: Noted some commenters have said their Windows have a shipload more CA certs.)
However, I cannot understand why Apple has facilitated the embedding of these government-linked Certificate Authorities in Mac OS X.
Chunghwa Telecom’s ePKI Root Certification Authority certificate is included in multiple platforms including Android (since Gingerbread), Mozilla, Microsoft, etc.
Technically, they have been privatised for some time already, officially with the government owning less than 50%. Hence I omitted to highlight them. But yes, I agree, this and many other CAs are still a concern.
I’ve written a simple script to remove these from OSX: https://github.com/sammcj/delete-unknown-root-ca
Pull requests welcome, Don’t run unless you know what you’re doing, YMMV etc….
You are mistaken, all the certs you mentioned are included in windows as well. Just use google and you can find hints like this one http://blogs.technet.com/b/pki/archive/2011/03/13/deployment-of-the-new-federal-common-policy-ca-root-certificate.aspx for the federal common policy cert and this one for several others http://answers.microsoft.com/en-us/ie/forum/ie9-windows_7/i-can-not-log-onto-secure-websites-with-my-cac/a5f14942-80e0-4faf-88a3-cc730ac4348d?page=3 even the chinese one is implemented http://social.technet.microsoft.com/wiki/contents/articles/2592.windows-root-certificate-program-members-list-all-cas.aspx
And of course Windows is language agnostic. There are versions for certain markets, which maybe do not need particular certificates. OS X is available worldwide in the same version. I guess these certificates are installed so that employees from certain organisations which use Microsoft or Apple Hardware and use their intranet do not need to worry. Try opening the cert lists with different browsers under windows. FF provides more certs than IE, because IE is bound to Windows, which is agnostic as I mentioned.
The same CA’s appear to also be in iOS – http://support.apple.com/en-ca/HT204132 but I can’t find any way to block these. Does anyone know how to block on iOS?
Windows has ~400 root CA certs. OS X has 220. I’m not sure where you got 38 from.
Of the 400: Government of Hungary NISZ Zrt, Government of Saudi Arabia, NCDC, Government of Japan, Ministry of Internal Affairs and Communications, Government of The Netherlands, PKIoverheid, Government of Australia, Australian Defence Organisation (ADO), Government of Austria, Austria Telekom-Control Commission, Government of Brazil, Autoridade Certificadora Raiz Brasileira, Government of Finland, Population Register Centre, Government of France, Government of Hong Kong (SAR), Hongkong Post, Government of Hungary NISZ Zrt, … you get the idea. Oh and yes, Government of the United States of America, Federal PKI.
http://download.microsoft.com/download/1/5/7/157B29AB-F890-464A-995A-C87945B28E5A/Windows%20Root%20Certificate%20Program%20Members%20-%20Sept%202014.pdf
http://support.apple.com/en-us/HT202858
My Windows 8.1 has only 34 root certificates installed on it and I access multiple internet web sites daily without problem.
Pablo Moleri Do you use Internet Explorer? Other browser might have their own root certificates. Plus, most sites are already covered by the big ones, so if you don’t run across an exception, Windows will not add a new cert. This does not mean the cannot.
Stefan Keller Hi, I use mostly Chrome and Firefox. I know FF has it’s own repository but Chrome uses Windows certificates. I would like to know how it behaves with one of those goverment issued certificates, does anybody have a url?
Pablo Moleri https://www.iad.gov/events/access.cfm
Windows downloads new certs on the fly – I’m not sure how it determines when to do it.
I’m in Pablo’s boat. A user with Win 7 Pro, Windows Server 2008R2, two Windows 8.1 and a Windows 10 checking proprietary apps. 400? Fanboytastic
Adam, thanks for the links, by the way – I’ve been looking for that information all morning.
Michael W Heinz When you visit a website that requires that root CA. (But not with Firefox since FF has its own certs)
” Windows 7 PC has 38 Certificate Authority certificates installed. ”
This is outright false. My Windows machine reports having 350 root certificates installed,
Windows has nothing in place to prevent the user from installing certs galore. That’s the same as OSX coming preloaded? How so?
Alan Lucas So, you’re claiming I installed the certs myself. No.
The number of certs that Windows installs is infamous – and the subject of public concern for years. For example – this podcast was released in 2010:
“And you’ll remember, Leo, years ago, when to my horror I looked at the size of my own trust store in Windows, which IE was using, and just said, oh my goodness, I mean, there’s so many. Well, turns out there were even many more than that. Microsoft trusts 264.”
https://www.grc.com/sn/sn-243.htm
> For example, U.S. citizens may be concerned about their NSA (or FBI) spying activities. They are afraid about the NSA being able to break encryption codes.
No. Everyone should be concerned about Governments performing man-in-the-middle attacks. Not just american citizens. This is a global threat that has no borders.
You are absolutely right. I was just giving that as one example. Certainly I’m also concerned, hence the post. 🙂
Lai Zit Seng 🙂 I just reread my comment and realized I sounded a bit harsh. That was not my intent!
My Windows 8.1 has only 34 root certificates installed on it and I access multiple internet web sites daily without problem.
You are absolutely right. I was just giving that as one example. Certainly I’m also concerned, hence the post. 🙂
Technically, they have been privatised for some time already, officially with the government owning less than 50%. Hence I omitted to highlight them. But yes, I agree, this and many other CAs are still a concern.
Interesting the varying number of root certificates in Windows that people are reporting. I don’t use Windows as a primary platform, so I had looked into only one Windows 7 PC at work, and that had just 38 roots. Noted another commenter reports 34. Now looking at another Windows 7 PC, I count less than 30! On another matter, I had previously seen the Taiwanese GCRA certificate when I first investigated this matter, but the cert is no longer present the few Macs I have. Yes, there are possibly more government-linked root certs. Another example is Hong Kong Post (owned by the Government of Hong Kong, according to Wikipedia, but I suppose that just means China). At any rate, the point is really about how various government-linked certs have worked their way into the trusted store of our computers, the Mac in particular since that is what I’m most familiar with.
The certificate for itself does nothing. And Windows has a list of CAs it will install (without asking the user) once you visit a website that needs said CA. See this link for all available CAs on Windows: http://download.microsoft.com/download/1/5/7/157B29AB-F890-464A-995A-C87945B28E5A/Windows%20Root%20Certificate%20Program%20Members%20-%20Sept%202014.pdf
The only difference you showed is that Windows installs those CAs as it needs them while Mac OS X has them handy no matter what.
And if secret services are as bad, why would they use a cert with their name in it to grab your data? Wouldn’t it be easier to just make VeriSign give them a custom cert for that matter? Nobody would ever notice.
Pablo Moleri Do you use Internet Explorer? Other browser might have their own root certificates. Plus, most sites are already covered by the big ones, so if you don’t run across an exception, Windows will not add a new cert. This does not mean the cannot.
Stefan Keller Hi, I use mostly Chrome and Firefox. I know FF has it’s own repository but Chrome uses Windows certificates. I would like to know how it behaves with one of those goverment issued certificates, does anybody have a url?
Pablo Moleri https://www.iad.gov/events/access.cfm
The certificate for itself does nothing. And Windows has a list of CAs it will install (without asking the user) once you visit a website that needs said CA. See this link for all available CAs on Windows: http://download.microsoft.com/download/1/5/7/157B29AB-F890-464A-995A-C87945B28E5A/Windows%20Root%20Certificate%20Program%20Members%20-%20Sept%202014.pdf
The only difference you showed is that Windows installs those CAs as it needs them while Mac OS X has them handy no matter what.
And if secret services are as bad, why would they use a cert with their name in it to grab your data? Wouldn’t it be easier to just make VeriSign give them a custom cert for that matter? Nobody would ever notice.
Windows has nothing in place to prevent the user from installing certs galore. That’s the same as OSX coming preloaded? How so?
Alan Lucas So, you’re claiming I installed the certs myself. No.
The number of certs that Windows installs is infamous – and the subject of public concern for years. For example – this podcast was released in 2010:
“And you’ll remember, Leo, years ago, when to my horror I looked at the size of my own trust store in Windows, which IE was using, and just said, oh my goodness, I mean, there’s so many. Well, turns out there were even many more than that. Microsoft trusts 264.”
https://www.grc.com/sn/sn-243.htm
Windows downloads new certs on the fly – I’m not sure how it determines when to do it.
I’m in Pablo’s boat. A user with Win 7 Pro, Windows Server 2008R2, two Windows 8.1 and a Windows 10 checking proprietary apps. 400? Fanboytastic
Adam, thanks for the links, by the way – I’ve been looking for that information all morning.
Sounds kind of scary; are there ways to block or delete these certs on Win or OS X?
Lai Zit Seng 🙂 I just reread my comment and realized I sounded a bit harsh. That was not my intent!
Michael W Heinz When you visit a website that requires that root CA. (But not with Firefox since FF has its own certs)
So can someone clarify: every cert on the list can be used to SSL for any site? These seems to go across Mac & Windows as an issue. [Centralized] Certs have always seemed kinda ridiculous to me anyway, I’m sure it will all turn out horribly for everyone.
That is correct. 🙂
That is correct. 🙂
Hi,
You mention CNNIC, here is a story about their CA being used in a MITM attack.
https://lwn.net/Articles/637613/