|
BYD has good options and decent value proposition. | I recently bought a BYD M6. It’s a 7-seater electric vehicle. I’ll write a review on the car in a later post. For now, I just want to write about the ...
Zit Seng's Blog
A Singaporean's technology and lifestyle blog
|
Quiz time, what does SMRT stand for? | We love to complain about our SMRT. After the most defining moment of MRT breakdowns in Singapore last year, spanning a total of 6 days, the investigation into the 2024 ...
Technology
|
Total fail that a simple problem took out this ISP | The Internet broke for ViewQwest broadband customers on 31 May 2025. This comes after another severe disruption that begun on 30 April 2025, lasting a few days for ...
|
I'm surprised that I like the Royal Kludge RK100 quite a lot. | I normally don’t make a big deal about keyboards — not unless they’re particularly spectacular, like the Logitech MX Keys, which I’ve raved ...
|
ASUS' sleek Zenbook laptop line now has a model with Ultra 7 255H processor. | The Zenbook line of ASUS’ ultraportable series of laptops has been around so many years that its evolution through each generation ...
|
The ultimate home lab server for 8-bay NAS and to host multiple VMs. | This is my ultimate DIY NAS build of 2025. It packs 8x hot-swap 3.5-inch disk bays, a decent Pentium Gold 8505, 64 GB of RAM, and enough NVMe ...
|
The best 8-bay ITX case for DIY NAS projects. | I’ve built clunky NAS using tower cases in the past. However, for my NAS build this time around, I wanted something diminutive. Ideally, it would be something as ...
|
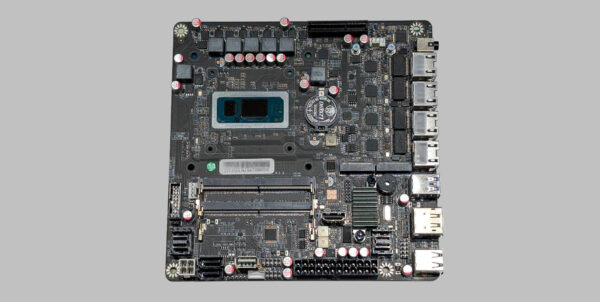
Excellent motherboard choice for a NAS and home server. | The soul of any DIY NAS system has got to be its motherboard. After deciding to build a new NAS a few months ago, I spent some time to research the parts I ...
|
The largely unplanned Wi-Fi, router, switch, PCs, NAS, and monitor upgrade. | We’re only two months into 2025, but I’ve already got quite a few home tech upgrades that I want to talk about. Many of them ...
|
Need the best Wi-Fi 7 for 6 GHz devices? | Got a fancy new laptop or smartphone with Wi-Fi 7? Looking to upgrade your home Wi-Fi to support them? ASUS has Wi-Fi 7 covered with several great options, such as the ...
|
Intel processors can have excellent battery life too. | Need an ultraportable with a seriously good battery life? These days, you’ve got quite a few choices. The new ASUS Zenbook S 14 UM5406 wants to add to ...
|
Powerful whole-home mesh Wi-Fi that's super easy to setup. | Whole-home Wi-Fi systems are often complicated to setup. eero stands out by enabling consumers who don’t have much network know-how to setup powerful ...
Other Posts
|
At times, I wonder, who owns the laptop. | This is mostly a rant. Our Ministry of Education (MOE) makes our students pay lots of money to buy a laptop and then cripple it so that basic things become so difficult to ...
|
Is now a good time to switch to EV cars? | Singapore plans to require all new cars from 2030 to be of cleaner-energy type. With just five years to go from now, people who are looking to buy a new car now face a ...
|
No need for brand loyalty with telcos. | StarHub was my first ever broadband provider. I’ve been their customer for over 20 years, even before the time Singapore began its Next Generation National Broadband ...
|
You still need to show your passport multiple times after all. | Changi Airport has fully implemented passport-less immigration clearance. It sounds cool not having to take out your passport and keeping it back safely ...
|
The current MRT disruption on the East-West Line is probably going to be the defining service disruption incident of 2024. Barring any further delays, we’re looking at just one day shy of a whole week of significant travel ...
|
Redefining success is less like a choice and more like a necessity. | Our new prime minister, Lawrence Wong, called on Singapore to embrace a wider definition of success. Netizens were quick to note, he probably meant ...
|
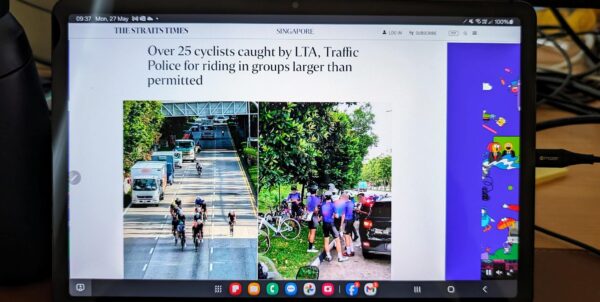
With all the bad press that LTA has been getting over their multitude of failed, failing, or destined to fail projects, this piece of news must have brought some cheers from motorists. They are stepping up their game to catch ...
|
Struggles with WordPress evolution over 20 years. | WordPress will be 21 years old this year. This blog, which originally existed as a hand-coded website, moved to WordPress just over 20 years ago. I’ve been ...
|
The gadget you need for a cinema-at-home experience. | Fancy a big-screen cinema experience at home? Get ready to be thrilled by LUMOS’ new AURO V2 home cinema projector. It’s a powerful, compact, ...
|
The detachable boom microphone is really awesome. | All the headphones and earbuds you’ve seen out there? They all seem to look somewhat the same. Until now. JLAB’s Work Buds manages to bring something ...