I’ve been using a password manager for a few years now. This is a tool that helps you store and manage passwords, and which typically integrates with web browsers to automatically supply and remember the correct passwords at various websites. Password managers, if properly understood, can help improve your online security, and I think everyone should consider using them.
Less than 5 years ago, I still wasn’t sold on to the value of password managers. I was still committing to memory all the various passwords I used at different websites. You may have heard the advice, don’t re-use your passwords on different websites. I don’t, though there are a couple of rare exceptions. I’ve devised a way to remember all my passwords.
However, it does get out of hand when different websites have different password complexity requirements. No, I don’t mean that their requirements are too complex, but that they specifically require simpler passwords because they can’t handle complex ones. Then, add on requirements on changing passwords, and not reusing old passwords when changing them, I eventually gave up trying to overwhelm my decaying memory.
In theory, password managers are great. You offload your memory to the application, or cloud service. It is, arguably, better than writing passwords on scraps of paper, or even in a little black book. But being involved in IT security, both in work as well as in my personal interest, I see that password managers have some inherent risks too. It’s like putting all your eggs in one basket. That basket can break, and you lose all your eggs at one go.
There are clearly some trust issues with password managers too. How do you know the application isn’t leaking your passwords elsewhere? If you chose a cloud service, how do you know the service provider won’t peek at your passwords? Cloud-based password manager services may tell you that they use end-to-end encryption, that at no point are plaintext passwords available to them, but how do you know this for sure, and why should you believe them?
Then, even supposing the fellas behind the password manager product or service are good, that doesn’t mean they are competent. How do you know they won’t get hacked, that malicious attackers can gain control of their product or service to steal your passwords?
Perhaps you’re now worried about password managers, and you begin to understand why I took so long to accept them. Well, while these are certainly points of concern, there are also so many other things to worry about. The question would then be, if the risks with password managers are worth the benefits they bring to you.
There are notable benefits of password manager. The usual feature list will include automatic generation of random passwords, so that each website you visit will have a totally unrelated password for your account. This is important, because if one website is hacked, and if they were bad enough to have stored your plaintext password, it’s useless to the attacker. Password managers also help you automatically enter your complex random passwords at websites, so the randomness of passwords isn’t a hassle to type, even if you don’t need to remember them. You only need to remember one very strong password to gain access to your password manager, and this shouldn’t be too much to ask.
With the rising trend of phishing attacks targeted at stealing account credentials, I see another cool benefit of password managers. If you train yourself to never manually enter passwords, even if you know them, at websites you visit, and instead let your password manager do the job, you may be protected against supplying credentials to fake websites.
Some of the new attacks are getting quite ingenious. This punycode attack, for example, could have worked even on people who carefully checked URLs in their browser’s location bar to ensure that they’re at the correct website. This attack has since been thwarted by Chrome and Firefox, but you know what, a password manager would also have refused to supply your account credentials to such a site.
Now, if you’re ever concerned about falling prey to phishing attacks, which is definitely a growing risk considering how clever the schemes are, your password manager may be able to save you. Even careful persons can get tricked, an accident or mistake waiting to happen.
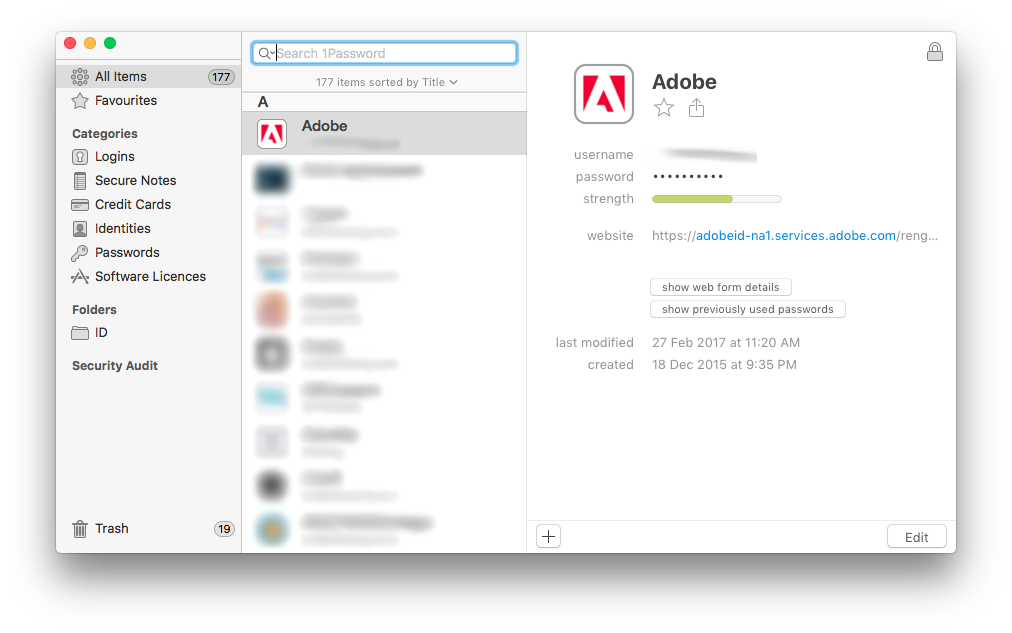
For those interested in my password manager of choice: it’s 1Password. It’s one of the mainstream password managers that can work completely standalone. Although the company behind 1Password, AgileButs, now offers a cloud-based service, I can use my 1Password without any dependency on the Internet or the services provided by them. In other words, I can get access to my passwords even if the Internet is down, or even if the company closes down. Of course, if AgileBits closes down, I don’t get any more software updates, which isn’t a good thing, but certainly not as bad as losing access to my passwords.
Although standalone, 1Password can synchronise its database through DropBox, so you can have multiple installations of 1Password on different computers and mobile devices all having access to the same passwords. For people like me who don’t even want to depend on DropBox, 1Password can leave it to the user to sort out their own synchronisation mechanism.
What password manager to choose definitely requires careful consideration. But perhaps a greater hurdle is deciding to adopt a password management solution.
I have been using keepass (Windows) for 10 years, also using keepassx (Linux) and keepassDroid (Android). I manually sync among my devices. Never store online. Keepass is open source.